
CYBERSECURITY MONITORING
SYSTEN GLORIA
SECURITY MONITORING SYSTEM GLORIA
Fleet-wide Cybersecurity Monitoring
Fleet-wide Cybersecurity Monitoring
Once the IT and OT systems of each ship have been studied, installing the necessary measures to make the fleet cyber resilient, it is necessary to implement a surveillance system capable of supporting the security control teams.
Based on SIEM systems, GLORIA offers greater flexibility in the observation of IT and OT environments, making it possible to detect key indicators of attack patterns, prioritise actions, relate data to their origin and manage all information centrally.

Advanced Threat Protection
In addition to GLORIA, CARMEN is capable of detecting Advanced Persistent Threat (APT) compromises from the intrusion phase. It uses advanced sandboxing and static analysis techniques to detect misuse
We assume that the organisation has already been compromised. CARMEN is in charge of collecting, processing and analysing outgoing and internal traffic, with the aim of identifying external movements towards control servers, recognising lateral movements for the maintenance of persistence or theft in the corporate network

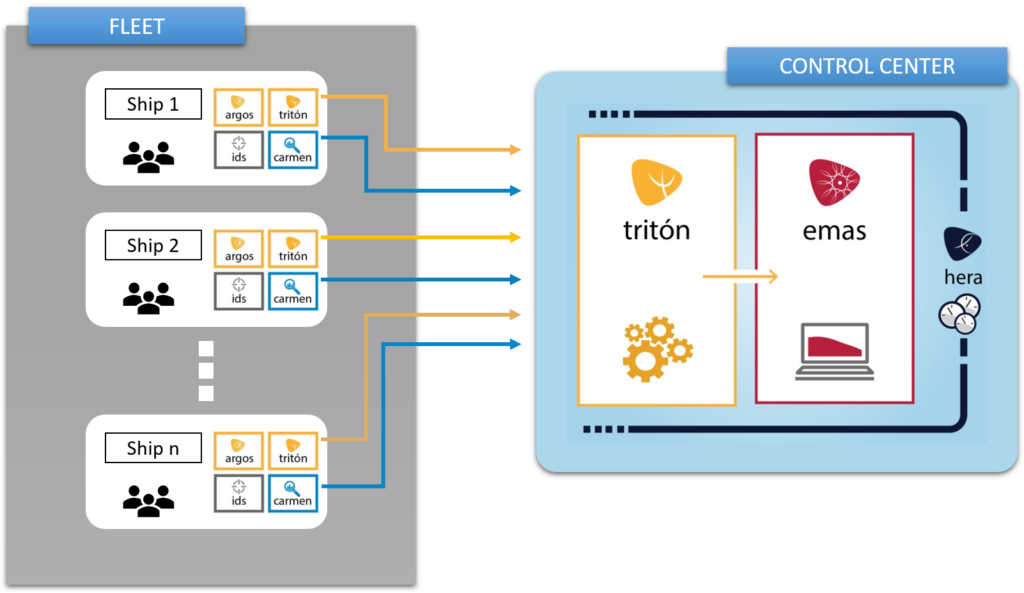
Installation on the Vessel
The necessary probes are deployed so that ARGOS collect information from all systems. TRITON and CARMEN analyse the information and create alerts, remediation and block suspicious traffic.
The installed software is autonomous and sends information when it has coverage.
Control Centre Installation
The TRITON module on the control centre receives the information from the on-board system.
The management console EMAS shows the status of each vessel’s assets and allows necessary action to be taken. HERA shows the internal and external reports with a summary of the fleet situation.
ISOC Monitoring
LThe ISOC smonitor 24/7 the status of each of the customer’s facilities.
Our technical staff constantly updates the system with new known threats. They apply remediation to emerging threats and advise the customer with recommendations for improvement of the security platform.




