The headquarters of a shipping company are where the critical systems of the organization reside, so it is extremely important protecting these shore-based centres against cyber attacks. These centres are pure IT environments and are easier to protect, as there are many cyber protection tools and companies with extensive experience in this type of equipment and systems.
It is possible to have other shore-based centres where IT environments converge with industrial OT environments, such as canning factories or automated warehouses. The treatment of these sites would be more like ships. For more information on how to protect mixed environments, you could review our article on Cybersecurity in Shipping- Ship Security.
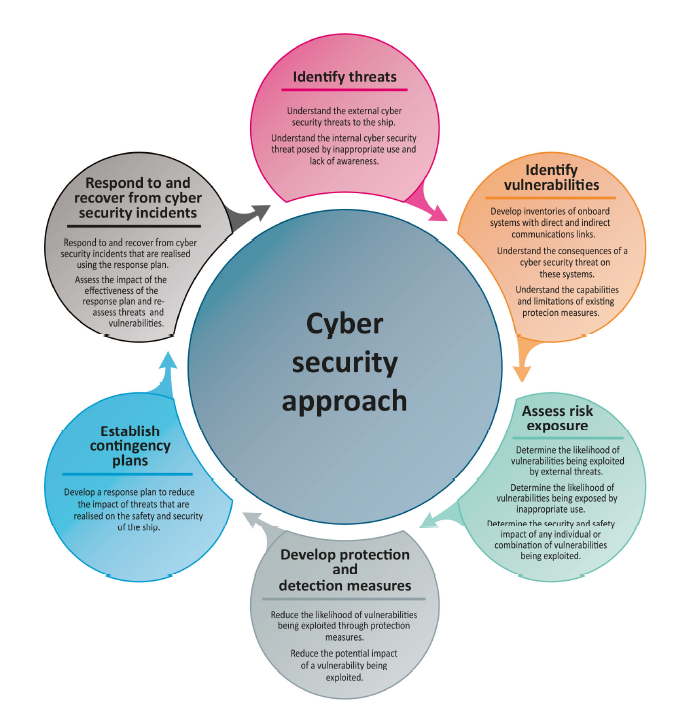
Phases to Protect Shore-based Centres
Cybersecurity is a critical part of a shipping company’s management, as disruption of operations can have serious consequences. Here are some of the steps that can be taken to implement effective cyber security measures:
Phase 1: Analysis & Regulatory Framework
- Understanding the infrastructure: Before implementing any security measures, it is necessary to study the technological infrastructure of the shipping company’s offices, including systems, networks, applications, and critical data. This study will help to identify vulnerabilities.
- Risk assessment: Once the assets to be protected have been identified, it is necessary to conduct a risk assessment to identify the potential threats and vulnerabilities of each asset. This will allow prioritisation of the areas that require immediate attention.
- Security policies and procedures: Develop cyber security policies and procedures that establish the security practices and standards to be followed.
In the case of shipping companies, it is necessary to create a global cyber security plan, so that the same policies and measures are applied to similar assets at all sites.
Phase 2: Actions
- Network segmentation: Dividing the network into separate segments limits the horizontal propagation of a cyber-attack in the event of a security breach. It is important to isolate networks with sensitive information or where critical systems are running, so that only uthorised persons have access to them.
- Installation of Firewalls and Intrusion Prevention Systems. Firewalls analyse the existing network traffic, recognise authorised users and restrict access to unauthorised users, i.e. they prevent and protect the network from intrusions or attacks by blocking access. Intrusion Prevention Systems (IPS) prevent unauthorised access to a computer or network by monitoring incoming traffic and checking it against an up-to-date database of known attacks. In case of a suspected threat, IPS can be configured to perform automatic remediation actions.
- Updates and patches: It is essential to keep all systems and software up to date with the latest security patches. Known vulnerabilities are often targeted by attackers.
- Access control: Implement access control systems to ensure that only authorised persons have access to critical systems and data. This includes two-factor authentication and secure password management.
- Education and training. This is one of the critical points of any cyber security system. Training employees on the company’s cybersecurity policies and guidelines, making them aware of common threats such as phishing.
- Incident monitoring and response. As we mentioned above, it is necessary to maintain the security level of a facility. This can be achieved by establishing a system of continuous network monitoring to quickly detect and respond to security incidents.
Phase 3: Continuous Improvement
- Incident Response Plan: regardless of the security measures implemented, it is necessary to design an incident response plan. This plan should include contain mitigation protocols for each type of incident that may occur, describing actions to respond to them, performing root cause analysis for each of them and defining recovery methods. It should also contain actions to be taken once attacks have been overcome to reduce the likelihood of reoccurrence.
- Audits and penetration testing: It is advisable to conduct regular security audits and penetration tests to assess the effectiveness of security measures and to correct possible vulnerabilities.
- Data backup and disaster recovery: Design secure data backup systems and disaster recovery plans to ensure the availability of critical data in the event of an incident.
- Continuous assessment: Cybersecurity is a continuous process. Security measures must be constantly reviewed and improved as cyber threats evolve.
Cybersecurity Expert Services Outsourcing
The complexity of securitization of a shipping company, in which centres with pure IT environments and ships with mixed IT/OT environments coexist, means that specific tools capable of analysing the threats and vulnerabilities of the two environments have to be implemented.
Gloria is a system that allows tracking of all IT and OT assets. It is a centralised system that helps the shipping company to analyse the situation of each centre from the office. Based on SIEM systems, it allows:
- Monitor mixed environments.
- Detect indicators of attack patterns.
- Prioritise actions.
- Track the entire life cycle of each asset.
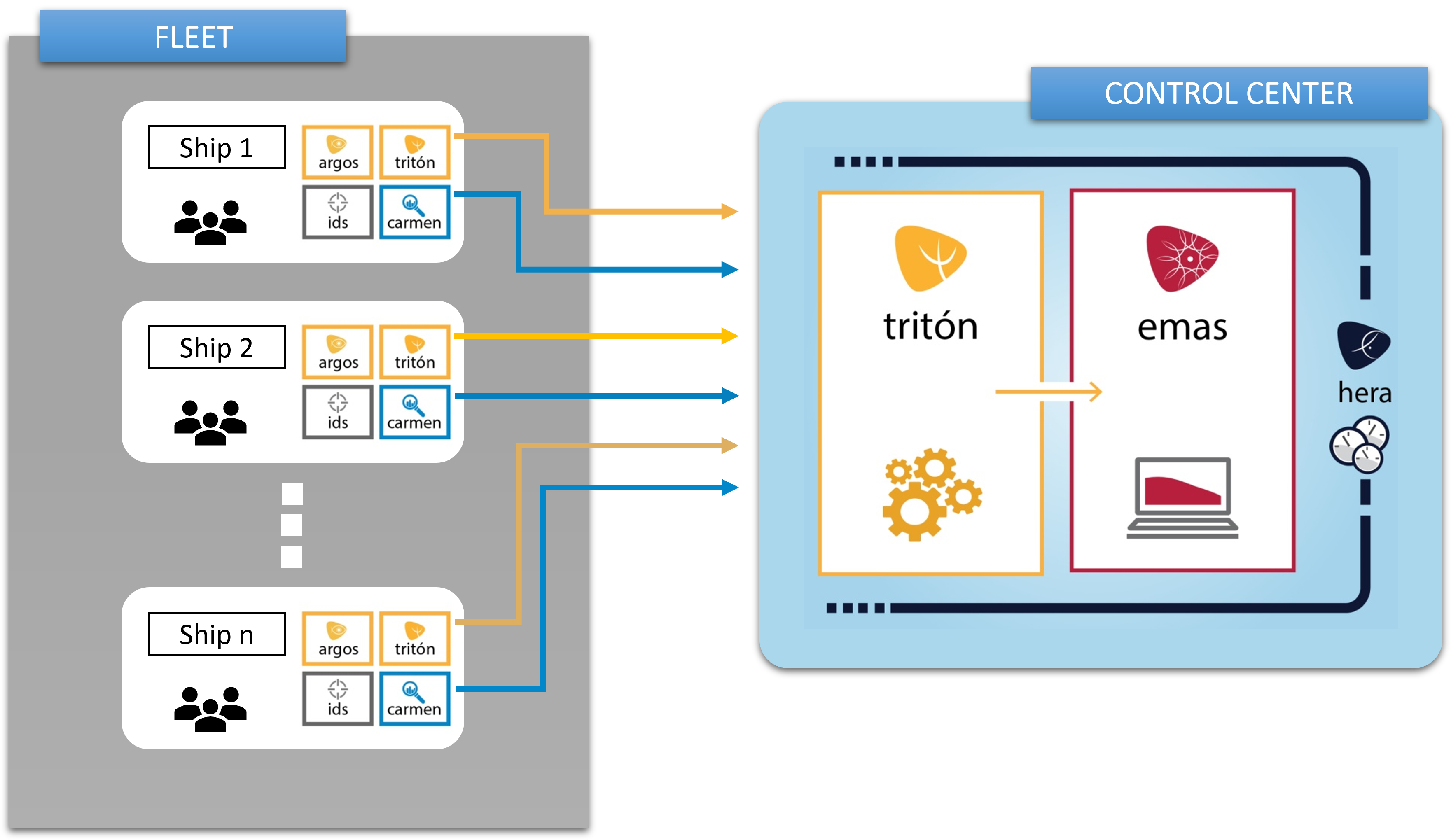
Gloria can be managed from our security centres, from which the cybersecurity status of each centre is monitored 24x7x365, applying new rules and responses to prevent known attacks before they occur at the customer’s facility.
furthermore, Aeromarine is able to offer consultancy services tailored to each centre and need, enabling our clients to meet security standards for new construction, operating vessels and shore-based brought-in centres.