Nowadays, maritime industry has changed to the point where is increasingly reliant on digitalization, operation integration, and automation. Heavy dependence on technology goes hand in hand with the increase of risk of cyberattacks. Prevention is an effective method of dealing with a cybersecurity risk, and it can be done from design. This article addresses what is cybersecurity by design in the shipbuilding industry, why should start at shipyard, and how Aeromarine can help to achieve it.
by Concha González, January 2023
What is Cybersecurity by design and why is it important?
Cybersecurity by design implies every system onboard is analyzed and selected from the cybersecurity point of view, guaranteeing its commissioning and integration with other systems are adequate.
As a result, the new building design and construction take on account any vulnerability that could compromise or result in the loss of confidentiality, integrity or availability of data or systems required to operate the ship or even the fleet operation. This may seem extreme but, in fact, it had already happened.
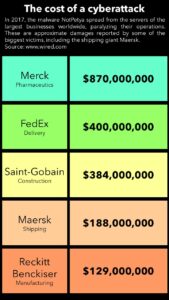
You can read in this article of Wired “The Untold Story of NotPetya, the Most Devastating Cyberattack in History” by Andy Greenberg how Maersk’s core services regained certain degree of normalcy more than one week after a cyberattack. During that time Maersk could not to read the ships’ inventory files of hundreds of container vessels arriving in their harbors nor take orders through maerskline.com for new shipments. Maersk’s 76 terminals were down from Los Angeles to Spain, Rotterdam, and Mumbai. Cranes were sitting idle, and tens of thousands of trucks were turned away. Final recovery took place after months.
An approach to avoid these situations is handling fleet cybersecurity from shipyard. Cybersecurity by design:
- Starts with the design concept of the ship, follows with requisitioning to suppliers and ends with the delivery of the vessel
- Analyzes all systems, even those which seem to have nothing to do with cybersecurity
- Involves shipowner, shipyard, vessel integrator, makers, suppliers, certifiers, and external consultants.
IACS Recommendation 166 on cyber resilience states guidelines for design and construction of new ships. Goals are to: Identify and understand all devices, systems, networks, and data flows on board. Protect OT and IT systems. Detect cyber incidents timely and effectively. Respond to cyber incidents to limit extension, effects, and possible damages. Recover functionality.
Shipbuilding Cybersecurity stakeholders and their roles
Class Societies
Since January 2021, newbuilds at shipyards are subject to IMO Resolution MSC.428 (98) which requires ships to account for cyber risk management in their safety management systems. According to IMO, Class Societies had released requirements and guidelines as the following:
- DNV-GL offers cyber secure class notation for classification. It establishes requirements for vessels and offshore units in operation and newbuilds across different segments and security levels: Cyber Secure, Cyber Secure Essential, and Cyber Secure Advanced.
- Bureau Veritas provides NR659 Rules on Cyber Security for the Classification of Marine Units to different class and levels notations: Cyber Managed Prepared, Cyber Managed, Cyber Secure Prepared and Cyber Secured.
- LLoyd’s Register has developed also ShipRight-Digital procedures and rules which can be found at its web site.
Owner
Shipowner follows its Cyber Security Policy before contracting the ship to the shipyard. Thus, shipowner’s requirements must be in keeping with their internal Policies and legal regulations. Also, shipowner will require from shipyard that the new building will be in accordance with IACS Recommendation 166. Shipowners want to ensure that design, integration, and maintenance of computer-based systems on board support secure operation. Therefore, there are means to protect against unauthorized access, misuse, modification, destruction, or improper disclosure of information. Information can be either computer-based aboard information or information transported through local vessel network and remote on-shore networks.
Shipyard
Shipyard is responsible of systems installation and design deliveries. Requirements are focused on correct design, proper request and purchase of equipment from suppliers, and compliance with regulation, certification, and shipowner requirements. Compliance includes inventory of assets and assessment of levels of criticality. This assessment can vary the design of systems, equipment, and even the network. Shipyard also needs proof of implementation and tests to verify functional and cybersecurity requirements.
Vessel Integrator
Vessel network integrator is responsible of interconnecting and integrating systems and equipment ordered by shipyard and shipowner including OT, IT, and computer networks. Coordination from design to commissioning with suppliers is also one of its duties. Suppliers usually propose pre-integrated systems; in that case, vessel integrator pays attention to connections and compatibilities and adapts network design and complexity. Vessel integrator tunes physical and logical network topography and traffic, defines accounts, privileges and remote connections. It restricts media use or resources, establishes malware and security policies and protection, monitors vulnerability and network communication. Also, vessel integrator has to obtain, supply and maintain cyber risk assessment and procedure documentation for both IT and OT systems.
Suppliers
Suppliers are responsible for proving equipment, devices, or systems to the shipyard according to purchase orders and their clauses. From the cybersecurity point of view, suppliers must deliver not only equipment, but also documentation. This documentation has to state the suitable processes, methods, techniques, and tools implemented to manage cyber risks.
External Consultants
External consultants assist shipowner, shipyard, and suppliers to go along to achieve cybersecurity goals. They
- Help shipowner and shipyards to make confident and technical decisions from requisitions to selection of products, equipment, and systems before commissioning.
- Guide suppliers to ensure their products are compliant to cybersecurity standards.
- Perform cybersecurity tests and trials before certification and collaborates with vessel integrator to solve any default or weakness.
Aeromarine, as an external consultant, helps to ensure new constructions comply with requirements. To do so, Aeromarine collaborates with stakeholders throughout all phases, helping them to identify and comply with cybersecurity requirements.
Before shipyard requests equipment from suppliers, Aeromarine can guide on contract clauses and selection through the prism of the cybersecurity. After procurement, Aeromarine analyzes initial documentation from suppliers to determine if the system must fulfill cybersecurity requirements; guiding them on how to prepare documentation. At the request of the Shipyard, Aeromarine collaborates with vessel integrator checking against the requirement to verify the final design. Also, we perform relevant tests on board at shipyard aimed at finding weaknesses prior certification such as vulnerability scanning, firmware screening, accessing control tests, authentication trials, software modification or anti-virus exams. Finally, Aeromarine delivers a full report to the Shipyard, suggesting measures of improvement or possible solutions if necessary.
Tasks in shipbuilding cybersecurity by design: identify, check and test
Actions to achieve cybersecurity goals summarize on three main tasks: identifying what systems are vulnerable, checking and testing them.
Identifying vulnerabilites
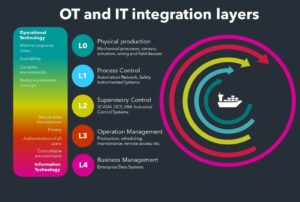
Onboard, there are two interconnected technologies that contribute to operate and maintain the ship in a safe condition:
Information Technology (IT): Devices, software and associated networking focus on the use of data as information.
Operational technology (OT): Devices, sensors, software, and associated networking monitor and control onboard systems.
It is important to analyze all IO and OT documentation provided by shipyard and suppliers with the goal of identifying what systems are vulnerable from the cybersecurity point of view. If you take no measures and IT or OT systems are attacked or suffer a disruption, human and vessel safety as well as the marine environment can be affected.
Common cyber vulnerabilities
Without being exhaustive, the following systems are usually installed on new ships:
- Global Positioning System (GPS), Electronic Chart Display and Information System (ECDIS) and the Global Navigation Satellite System (GNSS) are crucial enablers for navigation.
- Integrated bridge systems (IBS) link systems to provide all the details of ship’s navigation at one place. The data handled includes information such as Autopilot, Radar, AIS, ECDIS, ARPA radar, position, speed, rudder angle, depth, or propulsion data.
- Automatic Identification System (AIS) monitors and assists on maritime traffic. It operates on ships and shores to notify port and maritime authorities of ship’s location.
- Very Small Aperture Terminal (VSAT) allows a high-speed data satellite transmission, which makes possible on-board services such as Internet, Weather Forecast or Wireless Integration.
- Integrated Automation Systems (IAS) integrates the functions of control, monitoring and alarming of mostly all systems on the ship, including crucial propulsion equipment. It combines IoT (internet of things) networks on a distributed and redundant system. These Control systems can widen to main engine, generators, ballast tanks, life support, fuel and oil pumps, watertight doors, fire alarms and controls, cargo hold fans and environmental controls.
In any of the systems above, common cyber vulnerabilities as the following may be found, even on some newbuild ships:
- inadequate security configurations and best practices, including ineffective network management and the use of default administrator accounts and passwords
- absence of boundary protection measures and segmentation of networks
- permanent remote connection of safety and critical equipment with the shore side
- inadequate access controls to cyber assets, networks etc. for third parties including contractors and service providers
Therefore, identifying any possible vulnerability at any of the systems on board is an important task. As a result of it, some systems will be dismissed and others will be selected to comply with cybersecurity requirements.
Checking systems and their integration
After identifying vulnerabilities, first thing is to check measures to prevent vulnerabilities at system/equipment level; afterwards it is necessary to check systems integration in the new construction and the measures and procedures to prevent, mitigate and respond to possible cyberattacks at his upper level. This phase shall end up with a complete system (including standalone components) ready for on board cybersecurity tests to verify cyber resilience.
During this process, the following issues should be addressed:
- Identification and authentication: user identification, authentication policies, remote user access, external application access, account management, credential policies, system use notification and wireless access management.
- Use control: control for portable and mobile devices, remote and local sessions control, event audit, timestamp, permissions, and privileges policies.
- Integrity: data transmission integrity, third party communication, input and output validation, session integrity, security validation, malicious code protection, detection, and mitigation.
- Updating: change of software or configuration management and policies.
- Confidentiality: encryption during transmission, cryptography, algorithms, and keys.
- Data Flow: network segmentation and interconnection, zone boundary protection, application partitioning.
- Resource availability: DoS management, critical tasks priority, backup control and policies, recovery and reconstitution control and policies, emergency procedures and functionalities.
Testing cybersecurity by design in the shipbuilding industry
Testing is an effective way of verifying a cybersecure designed network. These tests are done at shipyard before the vessel is approved by the class certification society and before is delivered to shipowner. Since Class Society performs tests to approve the entire vessel network system too, pre-approval tests made by the Vessel Integrator or the External Consultant may reveal weaknesses or even faults which can be solved before compliance.
Examples of verification tests may be:
- Survey physical security
- Network storm
- Default credentials
- Station and access-control lock down
- Anti-virus testing
- Intrusion detection system (IDS)
- Network segregation
- Penetration testing
- Firmware screening
- Configuration changes test
During testing and in-between tests, network should be protected. Test procedures have to be documented and this documentation must be submitted as part of the required documents for approval. Moreover, shipower probably will do regular cyber tests during operation and results will be part of a consistent cybersecure network management.
Conclusions
Cybersecurity by design in shipbuilding implies cybersecurity decisions and actions during design, construction, commissioning, acceptance, and operation of a new building vessel. Cybersecurity by design not only secures vessel operation, but also provides means to protect against unauthorized access, misuse, modification, destruction, or improper disclosure of information.
Building a new ship under cybersecurity terms, involves shipowners, shipyards, suppliers, vessel integrators, certifiers, and external consultors; each one with different responsibilities and targets. Aeromarine, as external consultor, mainly helps shipyard to focus its efforts with regards to cybersecurity along the phases of shipbuilding until delivering.
There are three main phases. Firstly, identifying which devices, equipment and systems are susceptible of cyber vulnerabilities. Secondly, checking separately and integrated systems on access, integrity, or confidentiality. Finally, testing networks and systems to verify their sturdiness.
If you need more information, contact us.

